Today’s security landscape is drastically different than it was 5 years ago. The majority of IT services have been or are migrating to the cloud and an increasing number of employment positions are remote, even without considering the effects of COVID-19 and its variants. With this shift in service delivery and employment location, your perimeter has also shifted from an on-premises network with a defined perimeter, protected by a suite of controls; to your people and your ecosystem of customers, suppliers and partners (third parties). Again, your people and the external entities with whom you interact are your perimeter.
Focusing in on your third parties; Many organizations have built or are currently building robust third party risk management programs that cover the following areas:
- Security Risk
- Operational Risk
- Legal, Regulatory and Compliance Risk
- Reputational Risk
- Financial Risk
- Strategic Risk
Security specifically addresses loss attributed to data breaches, often in the following ways:
- Ensuring that third parties have appropriate technical and operational controls via vendor questionnaires and regular auditing.
- This will address data collection, processing, encryption, third party security stack, etc.
- Ensuring that third parties are addressing email spoofing and domain abuse via implementation of SPF, DKIM and DMARC.
- Ensuring that third parties are taking steps to reduce data exposure and man-in-the-middle attacks via SSL encryption, running up-to-date and patched software, and ensuring that only necessary ports are open and only accept port-appropriate traffic.
These risk identification and management techniques are typically delivered through vendors dedicated to profiling third parties, identifying their security maturity and overall risk, that is represented by some sort of risk score.
While these three general inspection areas are a great start, the ever-increasing threat posed by compromised third parties is not something that can be addressed by simply scanning their infrastructure for known vulnerabilities, assessing the state of their certificates, or ensuring that they have deployed DMARC in p=reject. The next evolution of third party risk management should include deep insight into the most active threat vector – email.
Third party risk management needs greater insight into email threats that originate from compromised third parties, or impersonate the same. In the below example, we have an email originating from a legitimate third party account, which has been compromised, and is now being used to send credential phishing emails, which are masquerading as a PO and eFax:
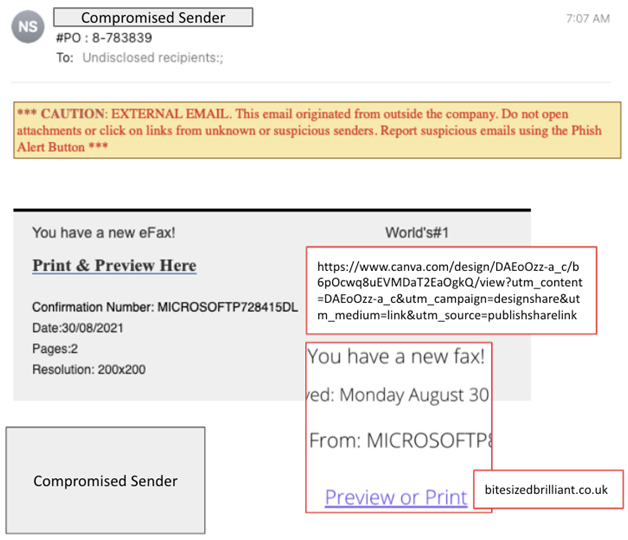
Message Context:
- Comes from a known external domain (good reputation)
- Comes from an unknown sender at that external domain (still good reputation)
- Sending infrastructure is O365 (good reputation)
- SPF and DKIM pass, while there is no DMARC record published for this domain
There are no hits on this third party organization via normal risk indicators, outside of the fact there is no DMARC record published for this domain.
The traditional method of assessing third party risk via email authentication does not account for email content or email intent. Email threats sent from compromised accounts will still show as successful messages from the point of view of SPF, DKIM and DMARC.
A strong ability to identify email threats, especially when such originate from compromised or impersonated third parties, offers deep insight into third party risk that is not present in today’s programs.
This insight will not only reduce risk for the organization as a whole, but also better-identify third parties who have suffered a compromise, even if said third parties are not yet aware of it, or an account compromise did not lead to data access and exfiltration that normally result in a broad disclosure.
Ultimately, detecting these types of threats consistently, while providing insight into the compromised third party, will improve your third party risk program and reduce risk across the organization.




