Vulnerability of Endpoints
The COVID-19 crisis has caused a prolonged work from home period, with some companies like Twitter and Fujitsu offering workers the opportunity to work from home permanently. While this is relatively easy to state, CIOs and CISOs have to adjust their IT networks to support this environment.
For users handling sensitive or classified information, a traditional endpoint system cannot be trusted when leaving the confines of the corporate/classified network.
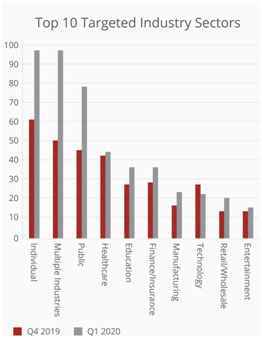
Hackers have been quick to take advantage of this shift. The figure to the right, taken from the McAfee Labs COVID19 Threat Report published in July 2020 shows how the attacks have increased by market sector. In just 10 cyber incidents during 2021;
- Over $600 million in cash was stolen or taken as ransom
- Tens of millions of citizen records were stolen
- 40,000 businesses’ IT operations put at risk
- At least one bank was effectively shut down for over a week
Traditional operating systems such as Windows, MacOS or Linux/Android that run on endpoints are vulnerable to cyber-attacks. Security updates and anti-virus software cannot be relied on to protect the endpoint. A compromised OS allows the threats full access to the endpoint, the sensitive data residing on the endpoint and the encryption keys that are used to protect the data.
A New Class of Secure Endpoint
A new protection solution is needed that can provide the following characteristics:
- Isolate the user’s sensitive work environment so that it is not exposed to network threats
- Protect sensitive data so that it is not compromised even if the laptop is lost
- Allow corporate assets to be protected from insider threats
- Facilitate monitoring of corporate assets and sensitive data that allow for remote backups, remote upgrades and remote disabling of sensitive data
- Identical user experience needs to a regular laptop

To achieve this, the OS and applications need to be housed in a secure virtual machine that has no direct access to the internet. Any data that flows to and from this domain is encrypted before it leaves. Any data stored on the endpoint is encrypted, and the encryption keys and algorithms are housed in their own secure domains. In some cases, the secure partition might be required to boot up only after the secure connection conditions have been met.
Traditional virtualization solutions are generally as vulnerable as the OSes that they are hosting and provide little protection against cyber-threats or data exfiltration. At no time is any sensitive data in clear text form in the unsecure domain.
The general anatomy of securing an endpoint’s connectivity to its backend infrastructure involves the following broad topics:
- Securing Data in Transit (DIT); The communication mechanisms (e.g. Wi-Fi, cellular etc.) used for backend connectivity are assumed to be inherently risky and therefore need to be secured. As part of the Commercial Solutions for Classified (CSfC) program, the National Security Agency (NSA) publishes Capability Packages (CP) for NSA customers to use Commercial Off-the-Shelf (COTS) products to build secure solutions. The Mobile Access (MA) CP defines the use of two layers of encryption (IPSec/TLS) to secure the connectivity between the edge device and the backend infrastructure
- Securing Data at Rest (DaR); A Self Encrypting Drive (SED), that supports Full Device Encryption (FDE), provides hardware encryption capability without taxing the compute within the edge device. SED necessitates the use of a PreBoot Authenticator (PBA) to unlock the SED on power-on. An effective way to mitigate DaR concerns is via the use of Virtual Desktop Infrastructure (VDI) clients to provide remote access to backend infrastructure
- Immutability of edge device configuration; Configuration immutability allows a system integrator to define an edge device configuration that meets security constraints, and deploy it with a fair degree of confidence knowing that the design configuration is not modifiable in the field
- Usability models; A secure edge device needs to account for security threats based on the usage model associated with the device. For example, a laptop which disallows the use of USB peripherals might be considered to be secure and yet be unusable by end-users.
Traditional virtualization solutions are generally as vulnerable as the OSes that they are hosting and provide little protection against cyber-threats or data exfiltration.
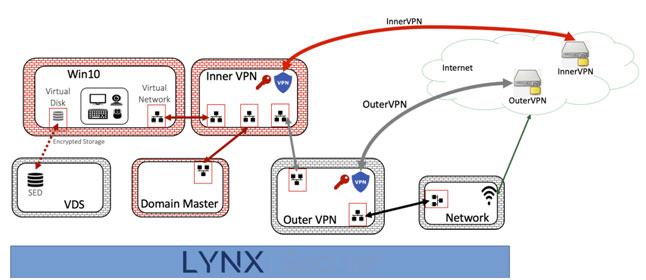
DiT is secured via a collection of VMs that implement a CSfC-compliant two VPN topology
- Network VM: Connects to the internet This VM is considered to be part of a black network and is hence insecure
- OuterVPN VM: Handles the outer-VPN functionality. The outerVPN is considered to be part of a gray network
- InnerVPN VM: Handles inner-VPN functionality. The innerVPN is considered to be part of a red network
- Win10 VM: Provides access to resources within the red network via the inner and outer VPN VMs.
- Domain Master VM; Handles remote manageability by integrating with a management controller (in the red network) and interfacing with the customer’s desired management framework
Customer Benefits
This approach for secure laptops has fundamental advantages as compared with systems built using traditional hypervisors. These include;
- This architecture does not include a privileged operating system that when compromised, can open up the system to vulnerabilities. This architecture does not have a hypervisor administrator login or an administrative user.
- A bad actor cannot do dynamic OS modification or try to execute code from the unsecure operating system into the secure operating system.
- Since the unsecure OS is isolated and partitioned from the secure OS, a denial of service attack on the unsecured OS would not affect the secure OS
- : The underlying software foundation preserves strict isolation between the different security functions and user-facing operating systems. A guest does not have access to another guest’s resources
- The security enforcement is guaranteed to be consistent with the security policy. With the configuration done before the boot, the data encryption is always on, the VPN can be configured to be always on and USB device insertion can be completely disabled.




