Everyone’s heard the adage that “compliance does NOT equal security.” For governance, risk, and compliance professionals, this means that while checking the boxes of scheduled, point-in-time compliance audits may pass muster with the regulators, it does not actually assure a mature enterprise security posture. Just because a company aced the assessment doesn’t mean that the company is immune from today’s expanding attack surface of threats and vulnerabilities.
For non-technical directors and C-suite officers, checking the compliance box has often been good enough to justify the security expense line on the P&L statement. When it came to security resource allocations, compliance certifications were about all anyone at that level had to concern themselves with or cast a vote for or against. But with the emergence of a network of connected devices, digital transformation, and the impact of the pandemic, compliance can no longer be viewed this basically. Corporate cultures must mature to the new paradigm of continuous compliance and security risk management, while recognizing the unsustainable consequences of failing to do so.
The frameworks themselves have risen to the challenge. The fundamental security processes and controls suggested by regulatory frameworks can now inform a strategic roadmap for ELTs and BoDs to adopt in their oversight and measurement of enterprise security programs.
Frameworks Can Inform Security Culture
Even if an individual enterprise is not required to follow certain regulatory disciplines, best practices and standards frameworks like NIST, ISO, and others can be followed for establishing security baselines that integrate governance, risk management, and security programs into business alignment.
This action gets to the heart of the greater spirit of the law of compliance – establishing and maintaining state-of-the-art security posture for the protection of all – versus the narrow letter of the law in just rubber-stamping certifications.
Here are the key steps to building a security program driven by compliance objectives:
Step 1: Adopt a best practices framework (e.g., the NIST Cyber Security Framework) that fits overall business alignment.
- Achieve board-level consensus to adopt and build a security program foundation through the appropriate framework, based on the standards that best fit the organization’s needs and industry profile.
- Conduct a self-assessment of the organization’s current state, or get a third-party assessment to identify gaps and establish a baseline against the framework.
- Involve all relevant stakeholders in assessment discussions to review the gaps and accept the findings.
- Create a remediation roadmap. Consider security risks to key information assets, and map those to future security and compliance needs.
- Prioritize remediation action steps based on risk values, immediate compliance needs, and resources availability.
The desired outcome is to build a security foundation and instill security controls/processes into the DNA of the company. Ultimately, compliance discipline sets the tone, and the compliance audit itself becomes essentially a non-event.
Step 2: After building anew spirit of compliance into the foundational program, satisfy the letter of the law with smart compliance governance.
Evolve to a more mature security posture by continuing to implement data security strategies at a program level, while maintaining prescribed compliance obligations.
- Create and adopt a governance model that provides continuous improvement to maintain security program alignment with the continually changing threat landscape.
- After mapping the requirements to a specific compliance framework, identify remaining requirements that might be typical to such compliance regulation. For example, certain controls in PCI, HIPAA or SOC2 are very specific to meet certain objectives. Build those additional controls.
- Maintain compliance by implementing formal policies/procedures and refine controls for all the key controls as needed to satisfy the requirements of the compliance standard.
- Develop measurement criteria and key performance indicators (KPIs) for continuous monitoring of the security processes that are put in place.
- Use these KPIs for a continuous communication loop from top to bottom and bottom to top, creating clear visibility for management on existing security risks.
With a compliance foundation in place, gain efficiencies by scaling process and control redundancies within multiple frameworks into the overall security program. As a starting point, the NIST CSF framework is recognized across industries. It balances structure and provides flexibility to allow an organization to build a security posture that best suits its needs.
The majority of compliance frameworks (PCI, HIPAA, SOC2, ISO, etc.,) share70-80% of security controls. Stricter and more industry-specific standards can be layered on top of NIST CSF to bundle the compliance obligations of multiple standards. Every organization is different, unique within its industry sectors, and will have its own framework portfolio.
This graphic depicts the enterprise level security program and some of its components based on the NIST CSF framework:
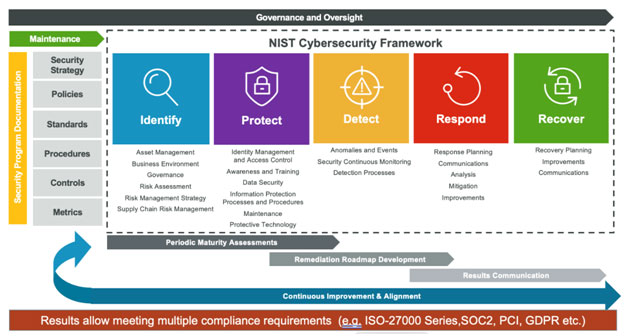
The Journey to Cyber Maturity
World events and technological paradigm shifts compel us to strike a careful balance between compliance and an effective security posture. A compliance-centric strategy achieves this synergy. Building maturity within a best-practice framework such as NIST CSF as a steppingstone to modern enterprise-level security programs can help most organizations achieve 75-80% of their compliance obligations. In such scenarios, compliance standards become both building blocks and byproducts of today’s comprehensive security programs.
Instead of thinking in terms of security versus compliance, a better option is to achieve security via compliance. Getting owners, managers, customers, and stakeholders to think differently brings us to the end of a paradigm shift, and to the next adventure on the cybersecurity journey.




